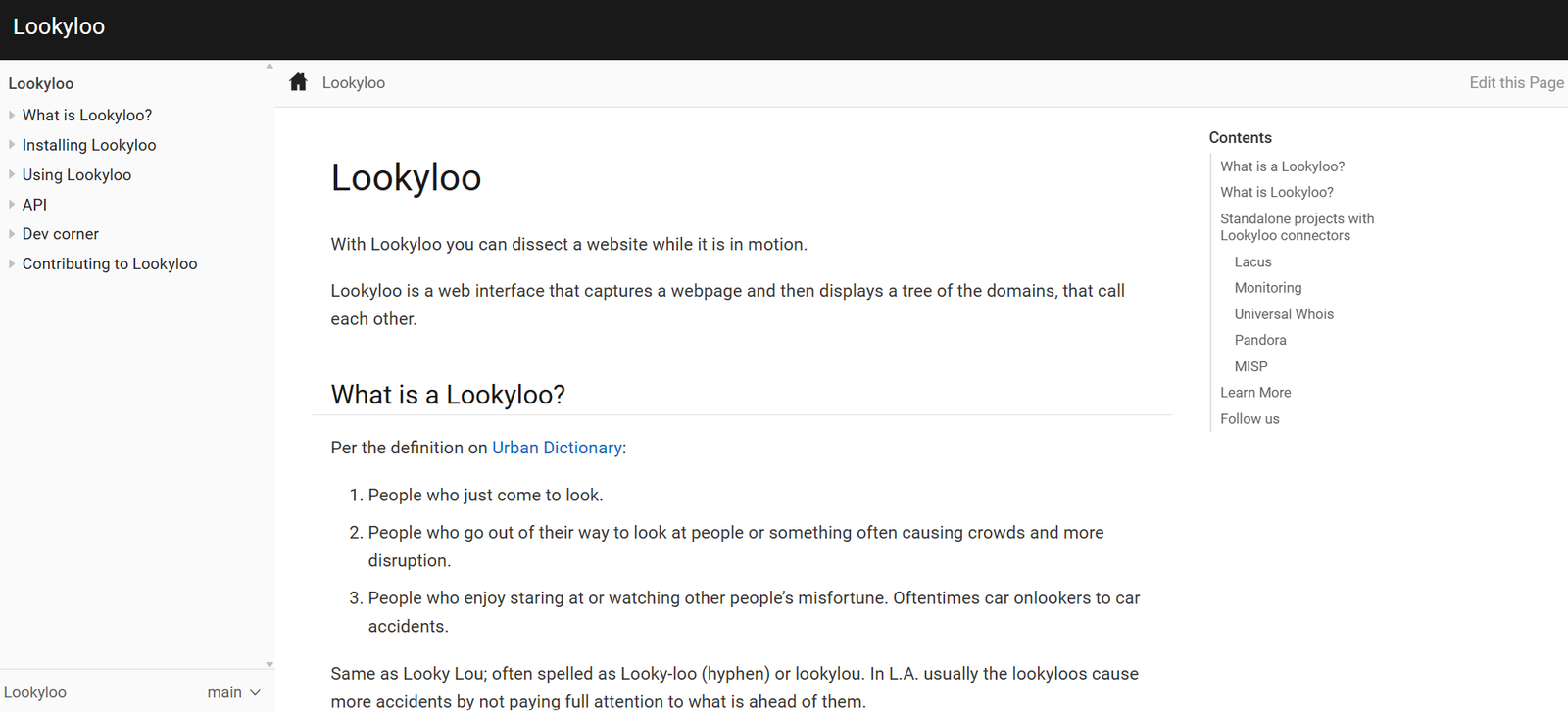
Lookyloo is an open-source tool designed to capture, visualize, and analyze the resources loaded by a webpage. Originally developed by CIRCL (Computer Incident Response Center Luxembourg), Lookyloo is widely used by cybersecurity researchers, analysts, and threat intelligence professionals to understand the hidden behavior of web pages. It helps uncover third-party scripts, redirections, trackers, and malicious content that may not be visible to regular users.
By providing a detailed visual tree of webpage resource calls, Lookyloo gives users an investigative view into how web pages behave and interact with external domains.
Features
Lookyloo offers a powerful set of features specifically geared toward web security analysis:
Webpage Capture: Load and capture the complete structure and behavior of a webpage, including scripts and third-party calls.
Visual Resource Tree: Graphical interface showing every resource the webpage loads and its relationships.
Third-Party Tracker Detection: Automatically highlights known tracking domains, advertising networks, and analytics tools.
Redirection Mapping: Detect and trace HTTP redirections, embedded iframes, and JavaScript-based navigation.
Malware & Phishing Indicators: Helps identify potential malicious behavior or phishing mechanisms through resource analysis.
User-Agent Spoofing: Customize the browser environment (e.g., user-agent, screen size) for more accurate investigation.
Sharing and Collaboration: Each capture can be shared via a unique link, allowing easy collaboration across teams.
API Access: Advanced users can automate Lookyloo workflows and integrate with existing systems using a RESTful API.
Privacy-Focused: Open-source and self-hostable to ensure full control of data and usage.
These features make Lookyloo a vital asset for cybersecurity professionals, digital forensic teams, and security researchers.
How It Works
Lookyloo works by simulating a real browser session to visit a given URL. When a URL is submitted, Lookyloo loads the page in a controlled environment and records every HTTP request and response, along with the structure of embedded content like scripts, images, CSS, iframes, and redirections. This information is then visualized in an interactive tree structure where users can explore domains, scripts, and the origin of each request.
The system also annotates known tracker domains and suspicious behavior, helping users identify threats or privacy risks quickly. Captures can be stored, searched, and shared among analysts for collaborative investigation or future reference.
Use Cases
Lookyloo has a variety of real-world applications in cybersecurity and digital investigation fields:
Threat Intelligence Gathering: Investigate malicious websites, phishing pages, or C2 (command and control) infrastructure.
Incident Response: Understand what resources a compromised or suspicious domain is serving.
Digital Forensics: Analyze how a webpage changes over time or under different configurations.
Tracker and Privacy Audits: Detect hidden trackers and third-party data collection on websites.
Academic Research: Study the behavior of online advertising ecosystems or web-based attack vectors.
Redirection Analysis: Follow complex navigation flows used in click fraud, malware delivery, or affiliate abuse.
These use cases make Lookyloo suitable for government CSIRTs, SOC teams, malware analysts, and researchers.
Pricing
Lookyloo is completely free and open-source, available under the BSD-3-Clause License. It can be:
Downloaded and installed for self-hosting.
Used via the public CIRCL-hosted instance for non-commercial research and analysis (with usage limitations).
There are no commercial licensing costs or subscription plans. Organizations seeking dedicated deployments can install Lookyloo on their own infrastructure to maintain privacy and control.
Strengths
Open-source & Free: No cost barrier for security teams or individual researchers.
Highly Visual: Interactive resource tree makes analysis faster and more intuitive.
Self-Hostable: Ensures data privacy, which is crucial for sensitive investigations.
Automation Ready: API support allows integration into threat intelligence pipelines or custom tooling.
Community-Driven: Actively maintained by CIRCL and supported by contributions from the security community.
Lookyloo’s strengths lie in transparency, usability, and its suitability for investigative work in digital security.
Drawbacks
Niche Use Case: Primarily focused on web resource analysis—may not serve broader security needs.
Requires Technical Setup: Self-hosting requires basic infrastructure and Linux familiarity.
Limited GUI Customization: The user interface is functional but not highly customizable for enterprise branding.
Not Designed for Non-Technical Users: Analysts without experience in web protocols or threat analysis may find the data overwhelming.
Despite these limitations, Lookyloo excels in its intended use case of web behavior analysis.
Comparison with Other Tools
Lookyloo can be compared to tools such as:
urlscan.io: Offers similar URL analysis with visual outputs, but is cloud-based and includes usage restrictions on the free tier.
VirusTotal’s URL Scanner: Provides threat scores and redirection paths but lacks the detailed resource tree and open-source availability.
Cuckoo Sandbox: Good for malware analysis but does not focus on visual web tracking behavior.
Lookyloo stands out for its transparency, local deployability, and visual breakdown of web page activity, making it ideal for advanced forensic use.
Customer Reviews and Testimonials
As an open-source project primarily used by security professionals, public reviews are limited. However, it is widely adopted within the threat intelligence community. Analysts frequently highlight its effectiveness in detecting hidden scripts, redirections, and third-party trackers. Cybersecurity researchers value its ability to share and reproduce web behavior across investigations. CIRCL’s active maintenance and detailed documentation have also been praised by the open-source and academic community.
Conclusion
Lookyloo is a powerful and unique tool for analyzing the behind-the-scenes behavior of web pages. Whether you’re tracking malicious activity, investigating phishing campaigns, or auditing trackers for privacy compliance, Lookyloo provides the tools to visualize and dissect web resource interactions in detail. Its open-source nature, intuitive interface, and forensic-grade features make it a valuable asset in any cybersecurity toolkit.